Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …
Some modern firewalls include SMTP flow control functions. When they detect what they perceive as anomalies, these devices disconnect the connection, unlike a mail server which would send back an explicit error message, justifying the non-receipt. This approach is inappropriate, as it does not comply with RFC 2321 and creates untimely blockages by generating errors during SMTP communications. These are the types of error messages we may receive:
SMTP timeout from remote mail server after sending data block SMTP timeout after end of data SMTP timeout after initial connection
These control systems, integrated into firewalls such as Cisco ASA and Stormshield, generate false positives. Rather than generating an SMTP reject code, the SMTP flow is simply interrupted, as is the connection as a whole. When the break occurs “after end of data” or “after sending data block”, i.e. following the transfer of part or all of the data, the reason for the block is probably to be found in the content of the message itself or in an attachment. Conversely, “after initial connection” indicates a break at the start of the SMTP dialog, following “HELO”, “MAIL FROM” or “RCPT TO”. Most of the time, this is due to a banned or incorrectly configured sender or recipient. This may concern the e-mail address itself, as well as the entire domain or IP address of the servers involved.
To prevent these false positives from being generated, and to avoid messages being inadvertently blocked, it is essential to disable these controls. To help you get started, we’ll explain how to set up two of the most popular solutions using this type of mechanism: StormShield SN and Cisco PIX/ASA.

It has a few specific functions, in particular, it restricts the scope of the SMTP protocol to its 7 main commands. Gone are all the ESMTP (Extended SMTP, an extension to the protocol) commands regularly used by recent mail servers (e.g. “SIZE”, which allows you to specify the size of a message before sending it, thus limiting traffic from over-quota messages). Another special feature is that it hides the SMTP banner. This information is the first response from the server during an SMTP connection.
As Cisco is, to our knowledge, the only company to hide this banner information, it enables a potential attacker to identify the range of firewalls used, which could be damaging.
Finally, it should be noted that message processing and protocol validity checks consume firewall resources, for a process that we believe is already carried out by our systems.
To deactivate MailGuard, you must be connected and logged in to the Cisco console, then type :
- configure terminal - no fixup protocol smtp 25 - write memory
Restart or reload the firewall to take these changes into account.
On Stormshield (or Netasq / Arkoon) solutions, controls are a little more complex to disable.
First of all, depending on your configuration, settings can be made in Global Policy (if you have several firewalls and/or use the SMC administration console) or Local Policy.
In “Security policy”, select “Filtering and NAT”, in the line authorizing contact with our servers, indicate “Firewall” in the “Security inspection” field. This disables packet content inspection, restricting filtering to the IP level.
Then, in the “Application protection” section, in the “Alarms” category, several rules are to be authorized:
– smtp:122 – Invalid characters in SMTP header
– smtp:217 – SMTP protocol overflow
– smtp:219 – Empty SMTP command line or response
– smtp:223 – SMTP command not supported by the server
– smtp:231 – Subject SMTP header contains non-ASCII characters
These alarms are used to secure access to your mail server. We believe that these protections are already offered by the Altospam solution and can only generate false positives and complicate the search for blockages in the event of reception problems.
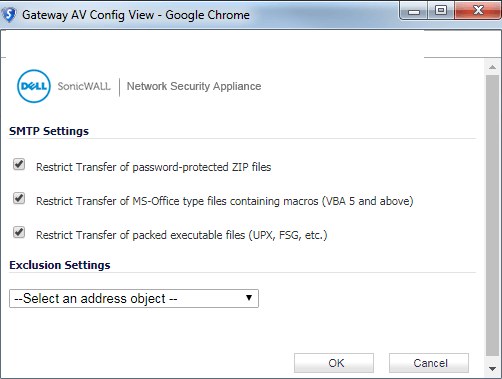
Dell Sonicwall solutions natively integrate an antivirus that monitors both HTTP and SMTP flows. This blocks certain types of file or content and may generate errors when messages are delivered.

Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …