Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …

A phishing email is characterized by a deceptive message. It presents itself as coming from a known sender, either a direct contact or a well-known brand or service, to give the recipient confidence. It encourages them to provide information, perform an action, click on a link or simply engage in a dialogue – in short, to “take the bait”. It’s a category of spam that uses identity theft. In most cases, it serves as an entry point: once the targeted data has been recovered, the spammer can take action that will have a major impact, whether it’s a new usurpation, embezzlement or direct theft of money in the case of banking data, or the installation of a viral threat if administrator access has been recovered.
Unlike most other spams, it exploits social engineering: it’s the recipient’s actions that activate the data leak. It’s a particularly nauseating process, because it implicates the end-user in the scam, against his or her will.
So it’s vital to know how to recognize a phishing email. Here are a few examples to help you identify it.
Probably one of the oldest and most common types of phishing email: “You’ve won €XXX!
These messages aim to retrieve personal information, and will ask for a copy of an ID or a bank account details. They often feature the identity of a legal profession, such as bailiffs or notaries, and multiply well-known icons or coats of arms.
There are two immediate points to bear in mind:
– Who is the sender of the message? Is this an area corresponding to the lottery concerned? Is the e-mail address I’m being asked to contact the lottery domain?
– Is the format consistent? Does this ad correspond to other messages I’ve received from this sender?
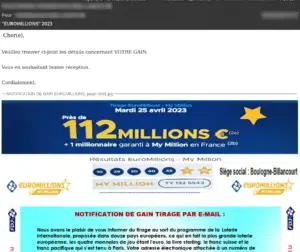
Example of a phishing e-mail presenting a Euromillions prize
This type of phishing directly seeks to recover your bank or company information. By reporting a false problem, it justifies the need to fill in a form or click on a link that will itself lead to a false web page bearing the effigy of the bank concerned.

Example of a phishing e-mail imitating a bank message. Office attachment integrates Wannacry ransomware
These phishing e-mails take the form of an injunction from an outside company to pay a non-existent invoice or some other fee. Sometimes they present small sums, as in the example above, so as not to alert the recipient. Nevertheless, they remain claims for undue sums and set a precedent that may have more serious consequences down the road.
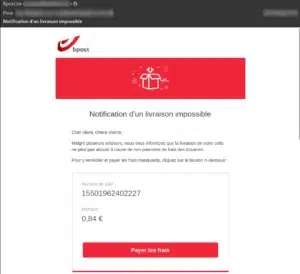
Example of a phishing e-mail presenting customs fees on delivery
This is a type of phishing email that has been on the increase in recent years. It takes the form of a threat of prosecution or summons, in connection with a criminal charge.
As in the case of fake lottery messages, they will instruct you to contact a so-called sworn agent: a judge, policeman or bailiff to settle the proceedings, within a strict deadline.
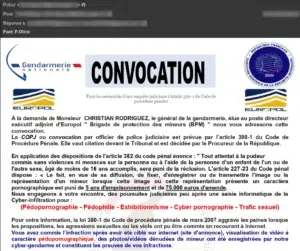
Example of a phishing e-mail impersonating the French National Gendarmerie for a summons to appear.
Spear phishing is a type of phishing that uses data known to the target company to refine its attack. It often targets a particular mailbox whose manager has a known role, and cites the well-known name of one of the company’s managers or executives to give, as before, an urgent, authoritative or familiar feel to the attempted scam.
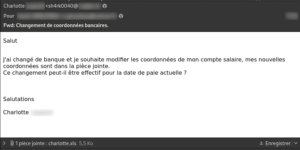
Example of a phishing email requesting changes to an employee’s bank details from the HR department. The attachment is infected with the Conficker worm.
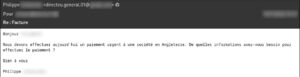
Phishing e-mail impersonating a company officer requesting banking information
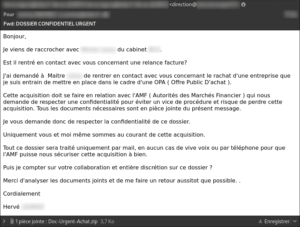
Example Phishing e-mail impersonating a company director about a company takeover project – The attached archive contains the Alureon rootkit.
There are several points to consider when reading a new message to identify a possible phishing attempt:
These stages are not mutually exclusive. A message can come from a known address, but still be phishing. It could be a spoof, or my correspondent’s address could have been hacked. Similarly, a well-crafted phishing email can look exactly the same as an original message from a sender.
The first three questions should raise any doubts. This doubt must lead to verification. If it’s a regular contact or a work colleague, you should contact them directly, using the usual means of communication and not those in the message, to validate their message.
If the issuer is well known, but has no direct contact, it can be contacted via the means indicated on its website, for example.
Finally, you can contact Altospam support. We can validate the message for technical anomalies or suspicious elements. In this case, we will take this message into account in our databases, to ensure that they are better identified in the future.
Protection against phishing e-mails is essential for your company’s security. These attacks can cause significant damage: theft of sensitive data, financial losses and damage to reputation. Here are some steps you can take to protect your company from phishing e-mails:
By adopting these best practices and making your employees aware of the dangers of phishing, you can considerably reduce the risk of successful attacks against your company.
Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …