Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …

When sending an e-mail from a Sender to a Recipient, the actual SMTP communication takes place between the mail server of the Sender domain and the mail server of the Recipient domain. In the case of ALTOSPAM, our servers interpose themselves on the path and retrieve the entire flow from the destination domain, retransmitting it after analysis to our customer’s mail servers. The purpose of this article is to explain the different rejection codes issued by our servers to those who send emails to our customers.
Different cases of email rejection
In the case of inbound filtering, the sender server is the one used by our customers’ users. These servers communicate with ALTOSPAM servers positioned in the MX fields of our customers’ DNS domains. In this case, the destination server corresponds to the recipient’s mail server at our customer’s site or at its host.
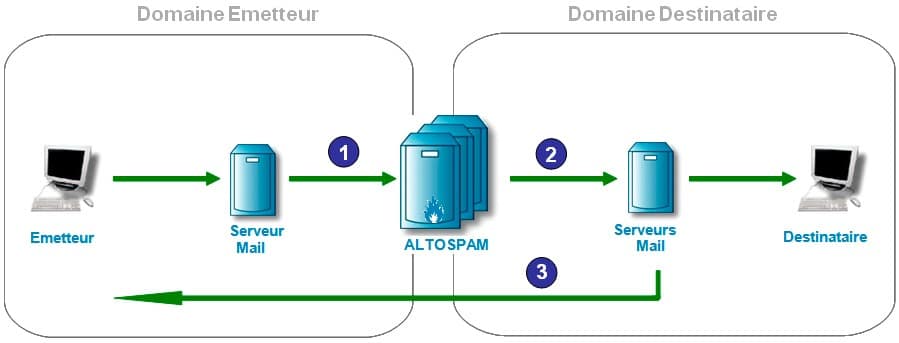
In this standard architecture, there are three cases of non-delivery of the mail to the recipient:
– Case 1: ALTOSPAM has blocked the e-mail for various reasons: virus, spam, attachment too large, etc…. In this case, ALTOSPAM performs a REJECT in the sense of the SMTP protocol. The sender’s mail server immediately receives an error code during the SMTP transaction, and can therefore send a non-delivery message back to the user. The following chapter details each of these cases and presents the various error codes.
– Case 2: ALTOSPAM accepts the e-mail, but the recipient’s mail server refuses it. In this rare case, we send a bounce https://www.altospam.com/glossaire/bounce.php to the sender to inform him of this blockage. We indicate in the generated bounce the error transmitted by our client’s server, so that the sender knows why his email could not be delivered.
– Case 3: It is also possible, if the recipient’s mail server does not respond directly during the SMTP transaction, that it accepts the message but is unable to forward it to the recipient (this is referred to as acceptance by the MTA, but refusal by the MDA). In this case, our client’s mail server sends a bounce directly to the sender to inform him that his message has been rejected. This is a rare case, as we do not recommend this type of setting to our customers (see Recipient filtering).
Details of Altospam reject codes
In the event of a refusal by ALTOSPAM servers, they systematically issue a permanent error code 5xx so that the sending server is informed of the refusal during the SMTP transaction and can notify the original sender. The aim is to allow the sender to be informed of the non-delivery of his email, and to be able to qualify the problem in order to resolve it.
ALTOSPAM rejects the following cases:
| Return code | Description |
| 550 “Unknown user!” | The e-mail recipient is not known to ALTOSPAM. The recipient’s mail servers relayed to us that the user did not exist. |
| 550 “HELO invalid!” | The sending server is not in FQDN (Fully qualified domain name) format. The server is only named as a workstation without a DNS suffix, it is considered as a Zombie and systematically refused by ALTOSPAM. |
| 550 “MAIL FROM invalid!” | The sending domain must be able to receive emails (at least on the abuse and postmaster addresses). It must have MX fields, and these MX fields must be host names (IPs are not allowed on MX fields). |
| 550 “RCPT TO forbidden!” | The recipient is part of a user list provided by the customer, as a prohibited recipient. |
| 550 “MIME error ([RAISON]) !” | The e-mail contains an attachment whose MIME encapsulation is indecipherable for the following reason: [RAISON]. |
| 550 “File attachment [EXT] prohibited!” | The sender has sent a prohibited attachment. [EXT] corresponds to prohibited extensions(details). |
| 550 “Virus detected: [VIRUS]!” | One of Altospam’s 5 built-in anti-viruses detected a virus in the e-mail. The e-mail contained the virus [VIRUS]. ALTOSPAM rejects the e-mail in its entirety. |
| 552 Too many recipients | The e-mail is sent to over 200 recipients at the same time. |
| 552 Failure Message exceeded limit | The mail is over 50MB. |
| 550 “IP blacklisted : Teer” | The source IP address is present in one of our blacklists. This blacklist only lists IP addresses that have sent too much spam in the last 15 minutes. |
| 550 >>> http://altospam.eu/?(…) >>> [FR] Hello, your message has been refused by the ALTOSPAM antispam platform to which your recipient is subscribed. Please use the above address to send it. [EN] (…) | Permanent rejection of an email considered as spam. The sender can click on a web address to release his own email after entering a CAPTCHA. This error return means that ALTOSPAM has considered the email to be spam, but still gives the sender the opportunity to unblock it. Once the sender has unblocked his message, his address is whitelisted in the Altospam customer account of the recipient domain. |
| 550 [FR] Hello, your message has been refused by the ALTOSPAM anti-spam platform to which your recipient is subscribed. It was considered spam. If this is not the case, please contact us. Thank you for your understanding! [EN] (…) | Rejection by teergrubing of an email that we are certain is spam, in which case the sender has no opportunity to release the email. This return code means that the e-mail sent is necessarily spam in our eyes. |
These return codes are given for information only. They may be modified at any time.
Altospam currently includes 16 complementary anti-spam technologies, combined with 5 anti-virus solutions. That’s why Oktey, the company that publishes Altospam, does everything it can on a daily basis to provide its customers with the best possible response in the fight against spam, avoiding false positives at all costs. Thanks to a configurable web interface, users can view all their email traffic and monitor Altospam’s performance themselves. If you have any doubts or questions, technical support is always available at altospam support.
Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …