Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …
The first step in securing your e-mail system is to install anti-spam and anti-virus software. The service used must be able to stop all types of malware, ransomware, polymorphic viruses and protect you from as yet unknown malware. This service must also block spam, phishing, scams and president and vice-president scams. especially have a false-positive rate extremely low (do not block legitimate emails). Service in must also offer very high availability and reliability. email retention in the event of downtime, with access to messages in waiting.
Regardless of functionality and filtering capabilities of your protection tool, it’s a good idea to add more, insure against email hacking,identity theft , confidentiality of communications and secure email flow to prevent circumvention (e.g. : man-in-the-middle). Communications compliance and privacy protection chain of trust between servers and the certification authority are also necessary to ensure good protection.
This article lists, in order of easy to set up, the various steps that will enable you to to achieve optimum e-mail security.
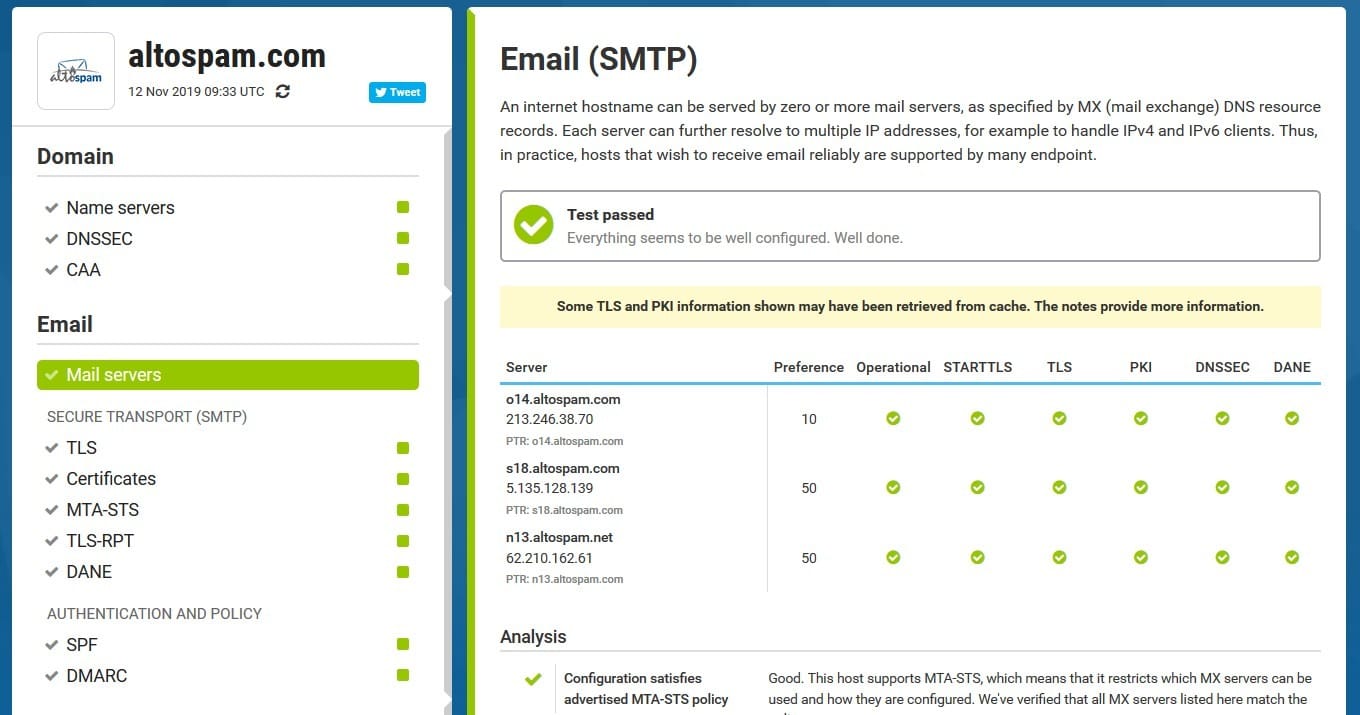
It’s important to have several secure MX servers in France, hosted by separate operators, supporting TLS1.0 to TLS1.3, managed on different replicated DNS zones and protected by DNSSEC and DANE. Here’s a detailed description of how set up your mail servers :
– It is imperative to have at least two MX per domain name. These MXs must be geographically located data centers and separate French operators, in order to ensure a seamless perfect service availability. On the other hand, as the Service du High Official of Defense and Security (HFDS) of the Ministry of Economy, when the servers are in France, communications are carried out within a and directly operational. In addition, the European Union provides a regulatory framework (RGPD) but also cooperation between states members.
– Mail servers must be highly secure and must support TLS1.0 communication, TLS1.1, TLS1.2 and TLS1.3 (latest standard). TLS1.0, although more PCIDSS-compliant since June 2018, must be retained for questions of interoperability with out-of-date servers. For example, Orange.fr is still unable to send TLS1.1 or TLS 1.2 emails!
– Encryption algorithms must be strong and not vulnerable, we recommend that you follow the OWASP ‘s recommendations, and to give priority to the strongest cipher available first (Cipher preference).
– The various MX must be managed by separate DNS zones, if possible hosted by two different DNS providers. To ensure very high availability, it is necessary to It is preferable to use MX servers managed on different domains, in order to not be dependent on a single DNS zone, because if DNS resolution doesn’t does not work, emails cannot be sent to the mailboxes.
– These different DNS zones must be protected by DNSSEC in order to secure DNS exchanges and prevent mail server substitution attacks. DNSSEC enables validate the authenticity of the response provided by the DNS server.
– Ideally, the must use a valid certificate issued by a reputable CA, implementingOCSP stapling to enable verification certificate by remote servers.
– Verification of conformity of certificates used for TLS must be ensured by implementing DANE on DNSSEC. DANE protects the trust between the server and the certification authority.
All Altospam customers benefit from all these recommendations, since their Internet mail servers are Altospam servers, themselves correctly configured in all these respects.
Now let’s take a look at all the possible areas for improvement once your mail servers are perfectly configured. The points below are listed from the easiest to implement to the most complex.
1. Create addresses: postmaster and abuse.
To comply with RFC 2142 and RFC 5321, we recommend that you create the addresses postmaster@votredomaine.fr and abuse@votredomaine.fr. These addresses can be aliases to the IT manager’s address. They are important because they enable anyone to contact an administrator in the event of communication problems or spam being sent from your mail server.
2. SPF, DKIM and DMARC
We strongly recommend the implementation of mail server verification protocols addresses. SPF identifies authorized IP addresses to send emails on behalf of your domain. DKIM digitally signs outgoing emails to ensure their integrity. And DMARC is used to specify the policy to be applied by the recipient in the event of SPF and DKIM non-compliance, and can also receive reports from non-conformity.
If you use our MailOut service (Altospam’s option), here’s what these fields might look like. For example In the absence of a fairly restrictive policy. It is also important to customize your SPF configuration if, for example, you are using a service provider for your emailings.
@ IN TXT "v=spf1 include:_spf.oktey.com -all" mail._domainkey IN TXT "v=DKIM1; k=rsa; t=y; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCwxd9+aNMru1CzIUe5hRLlnBkfOFtGnGdntEoSvJy7dyhSO638HJRJgM5UmSe5/qoCJemShO+h87uLlCGQIci2uHvUDjsrw2s2ygGroQZH6JANgDgV5OrPAHsBNURDE9zqzHLH1+RFyDdB6BGSkcfj2ekTGnhpgU05+84k24i2xQIDAQAB" _dmarc IN TXT "v=DMARC1; p=quarantine; rua=mailto:postmaster@votredomaine.fr; sp=reject"
3. MTA-STS and TLS reporting (TLS-RPT)
MTA-STS(RFC 8461) is an authentication mechanism for your MX servers. Its implementation by creating a sub-domain: “mta-sts”. page: “.well-known/mta-sts.txt” accessible via HTTPS. A titre For example, when using Altospam, this page should contain the following information:
version: STSv1
mode: testing
mx: *.altospam.com
mx: *.altospam.net
max_age: 2592000
The file in question can be accessed at https://mta-sts.votredomaine.fr/.well-known/mta-sts.txt. In this file, “testing” indicates that the configuration simply reports events. Once tested, to go into production, simply change: “testing” to : “enforce”.
To disseminate information, he It’s also a good idea to add a TXT field to your domain. The id for the policy is a serial number that generally includes the date updated :
_mta-sts IN TXT "v=STSv1; id=2019110801;"
TLS-RPT(RFC 8460) provides reports in the event of communication problems related to the use of TLS on your messaging system. The format of this field is example:
_smtp._tls IN TXT "v=TLSRPTv1;rua=mailto:postmaster@votredomaine.fr"
To evaluate DMARC and TLS-RPT reports, you can use an external service such as https://www.uriports.com/ or https://www.mailhardener.com/. These services concentrate all compliance reports in one place and automate analysis tasks.
4. DNSSEC
DNSSEC must be enabled on your DNS manager and at your domain registrar for DS registration (if different providers). For Altospam customers, DNSSEC is already active on our estates. However, to fully lock the chain, It’s best if your domain name is also secured via DNSSEC. On the other hand, the use of DANE on Altospam servers has had little impact on the company’s business. of interest if your MX fields are not themselves protected by DNSSEC. We will we strongly advise you to activate DNSSEC on your domain.
Once you have With all these elements in place, your messaging system will be optimized and secure.
There are online tools for diagnostics to ensure that these procedures are activated. Here are the ones we find most interesting: https: //www.hardenize.com/ h ttps://nstools.fr/ https://en.internet.nl/mail/ and https://aykevl.nl/apps/mta-sts/
Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …