Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …

Altospam and MailOut are real shields against threats to your e-mail. One protects the incoming flow, the other the outgoing flow. Combining the two protects you from the dangers of the Internet. Despite fast installation and effective protection, you may still have some questions about the first uses of our solutions. This article brings together a selection of frequently asked questions about our technical support.
Some companies don’t have an IT department, so installing our solutions can be confusing if you’re not familiar with DNS concepts. Our solutions are not installed on a workstation or on your mail server. These are SAAS solutions, so we protect all the email addresses in your domain name. All you need to do is change the MX records in your DNS zone. We have written an article on this subject which you can find here: https://www.altospam.com/actualite/2016/08/procedure-dinstallation-daltospam-mailout/
When you create or modify a record in your domain’s DNS zone, it may not yet be visible on the Internet. In fact, there’s what’s known as DNS propagation time, i.e. the length of time during which your modification is propagated throughout the global network. This DNS refresh can take up to 48 hours.
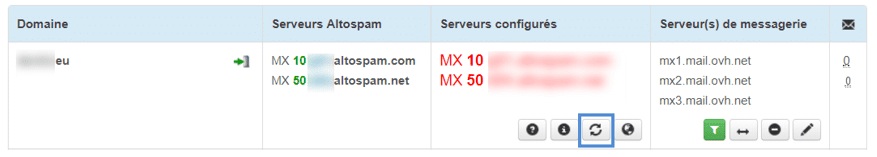
You can click on the button (framed in blue) to refresh the Altospam console.
The Altospam solution lets you add email addresses to your white or black list. It is therefore possible to authorize or block all e-mails from a particular person.

It’s important to distinguish between global lists and user lists. The global list is only accessible to the Altospam account administrator, while the user list is specific to each mailbox. This is not the only subtlety: the user whitelist takes precedence over the global list. What’s more, adding the same email address to both whitelist and blacklist will cancel the blocking of the address if it’s global, and the opposite if it’s user-specific.
The order of priority of the lists can be represented as follows:
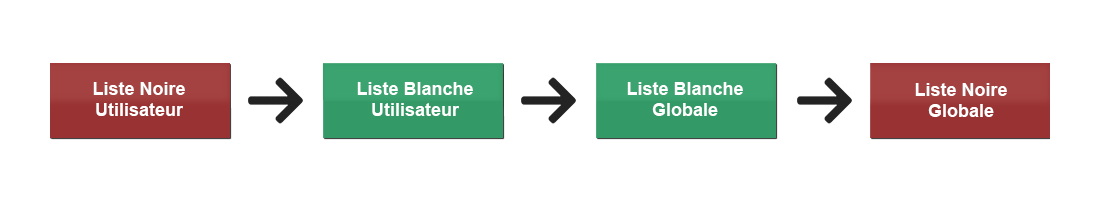
Prioritization of white and black lists
When you log on to the Altospam interface, you may see the following message:
Although not essential to Altospam’s operation, recipient filtering is a configuration option not to be overlooked. It blocks the sending of an e-mail to a non-existent user, thus preventing the generation of useless traffic both on Altospam’s servers and on your own. Here is a diagram that explains this concept very clearly:
We have written an article dealing in greater detail with the notion of destination filtering: https: //www.altospam.com/actualite/2017/04/filtrage-destinataire-serveurs-emails/
When you configure Altospam for your e-mail server, you only need to change the MX. This change implies a DNS propagation time of up to 48 hours. This value is theoretical, since spammers will delay their DNS refreshes as long as possible, which is why you may receive mail arriving directly at your door without going through our servers. Live spam is relatively common in the first two weeks after Altospam installation, but it rarely continues after that.
To avoid this, if you have your own mail server, you might consider restricting the SMTP flow to Altospam servers only. For details, see “3) Protecting your mail server” in the article: https: //www.altospam.com/actualite/2016/08/procedure-dinstallation-daltospam-mailout/
There are two ways to check that an e-mail has passed through Altospam’s servers. The first is to look directly in the headers of the received e-mail and check whether one of the “Received” fields contains an Altospam server or whether an “X-ALTOSPAM-HOST” field is present.
The second method is simply to use the interface we provide for our users and go to the logs section, then search for the email in question. If the e-mail is not present in our logs, it’s because it went live.
Once you’ve checked that the e-mail has passed through Altospam’s servers and that it isn’t advertising (we don’t block advertising e-mails that comply with the LEN), you can send us the
original e-mail
in
EML FORMAT
(or
MSG) FORMAT
to the spam address<at>altospam.com. It is imperative that this is the original e-mail and not a transfer, as the original e-mail headers must be present. If the e-mail is an advertisement and you don’t want to receive it, you can activate the anti-ad in the “settings” section. Details in this article: https: //www.altospam.com/actualite/2008/11/comment-nous-transmettre-les-spams-que-vous-recevez/.

Someone sends an e-mail to an address on your domain but receives an “unknown user” response. There may be two reasons for this, the first being that your mail server is reporting that the address is unknown. In this case, you need to look at what’s wrong. The second is that when your server returns that the user doesn’t exist, we store it in cache and refuse subsequent e-mails for that same address. If the address is created in the meantime, simply wait 1 hour, or contact our support team so that we can clear the Altospam server cache.
This article is designed to save you time in solving simple problems when installing Altospam. However, our teams remain at your disposal to answer any questions you may have. You can contact us by email at support<at>altospam.com or by telephone on 0825.950.038 (€0.18 incl. VAT/min).
Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …